How does Ethernet work? MII, GMII, RGMII interface advantages and disadvantages, Perform a loopback test, FII-PRA040 Altera Risc-V Tutorial Experiment 14
Experiment 14 Ethernet
14.1 Experiment Objective
- Understand what Ethernet is and how it works
- Familiar with the relationship between different interface types (MII, GMII, RGMII) and their advantages and disadvantages (FII-PRA040 uses RGMII)
- Combine the development board to complete the transmission and reception of data and verify it
14.2 Experiment Implement
- Perform a loopback test to check if the hardware is working properly.
- Perform data receiving verification
- Perform data transmission verification
14.3 Experiment
14.3.1 Introduction to Experiment Principle
Ethernet is a baseband LAN technology. Ethernet communication is a communication method that uses coaxial cable as a network media and uses carrier multi-access and collision detection mechanisms. The data transmission rate reaches 1 Gbit/s, which can satisfy the need for data transfer of non-persistent networks. As aRGMIIn interconnected interface, the Ethernet interface is very widely used. There are many types of Gigabit Ethernet MII interfaces, and GMII and RGMII are commonly used.
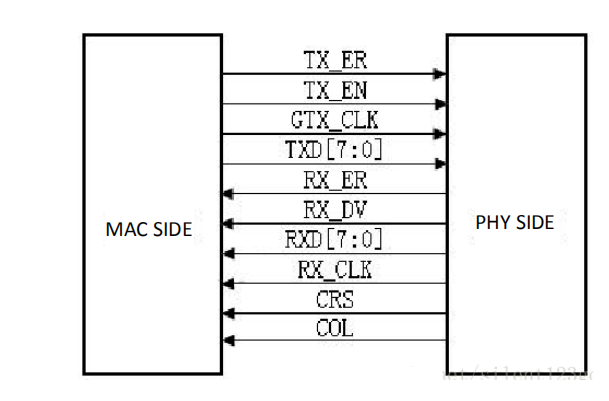
MII interface has a total of 16 lines. See Figure 14. 1.
RXD(Receive Data)[3:0]: data reception signal, a total of 4 signal lines;
TX_ER(Transmit Error): Send data error prompt signal, synchronized to TX_CLK, active high, indicating that the data transmitted during TX_ER validity period is invalid. For 10Mbps rate, TX_ER does not work;
RX_ER(Receive Error): Receive data error prompt signal, synchronized to RX_CLK, active high, indicating that the data transmitted during the valid period of RX_ER is invalid. For 10 Mbps speed, RX_ER does not work;
TX_EN(Transmit Enable): Send enable signal, only the data transmitted during the valid period of TX_EN is valid;
RX_DV(Reveive Data Valid): Receive data valid signal, the action type is TX_EN of the transmission channel;
TX_CLK: Transmit reference clock, the clock frequency is 25 MHz at 100 Mbps, and the clock frequency is 2.5 MHz at 10 Mbps. Note that the direction of TX_CLK clock is from the PHY side to the MAC side, so this clock is provided by the PHY;
RX_CLK: Receive data reference clock, the clock frequency is 25 MHz at 100 Mbps, and the clock frequency is 2.5 MHz at 10 Mbps. RX_CLK is also provided by the PHY side;
CRS: Carrier Sense, carrier detect signal, does not need to synchronize with the reference clock. As long as there is data transmission, CRS is valid. In addition, CRS is effective only if PHY is in half-duplex mode;
COL: Collision detection signal, does not need to be synchronized to the reference clock, is valid only if PHY is in half-duplex mode.
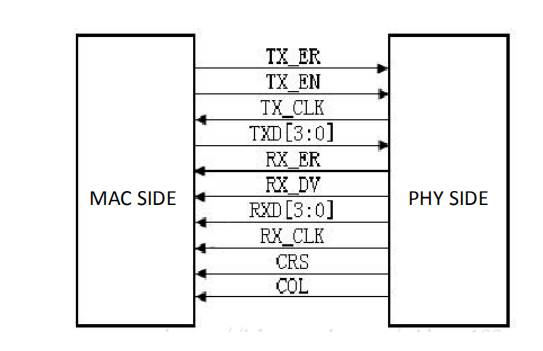
GMII interface is shown in Figure 14. 2.
Figure 14.2 GMI Interface
Compared with the MII interface, the data width of the GMII is changed from 4 bits to 8 bits. The control signals in the GMII interface such as TX_ER, TX_EN, RX_ER, RX_DV, CRS, and COL function the same as those in the MII interface. The frequencies of transmitting reference clock GTX_CLK and the receiving reference clock RX_CLK are both 125 MHz (1000 Mbps / 8 = 125 MHz).
There is one point that needs special explanation here, that is, the transmitting reference clock GTX_CLK is different from the TX_CLK in the MII interface. The TX_CLK in the MII interface is provided by the PHY chip to the MAC chip, and the GTX_CLK in the GMII interface is provided to the PHY chip by the MAC chip. The directions are different.
In practical applications, most GMII interfaces are compatible with MII interfaces. Therefore, the general GMII interface has two transmitting reference clocks: TX_CLK and GTX_CLK (the directions of the two are different, as mentioned above). When used as the MII mode, TX_CLK and 4 of the 8 data lines are used.
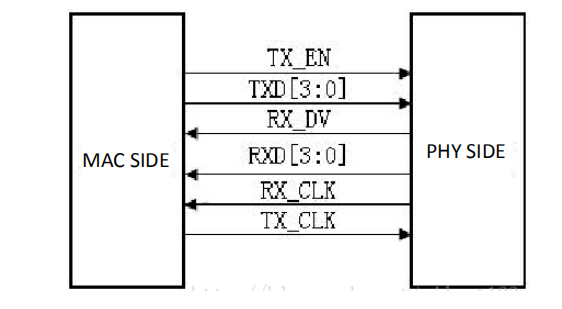
See Figure 14.3 for RGMII interface.
Figure 14.3 RGMII interface
RGMII, or reduced GMII, is a simplified version of GMII, which reduces the number of interface signal lines from 24 to 14 (COL/CRS port status indication signals, not shown here), the clock frequency is still 125 MHz, and the TX/RX data width is changed from 8 to 4 bits. To keep the transmission rate of 1000 Mbps unchanged, the RGMII interface samples data on both the rising and falling edges of the clock. TXD[3:0]/RXD[3:0] in the GMII interface is transmitted on the rising edge of the reference clock, and TXD[7:4]/RXD[7:4] in the GMII interface is transmitted on the falling edge of the reference clock. RGMI is also compatible with both 100 Mbps and 10 Mbps rates, with reference clock rates of 25 MHz and 2.5 MHz, respectively.
The TX_EN signal line transmits TX_EN and TX_ER information, TX_EN is transmitted on the rising edge of TX_CLK, and TX_ER is transmitted on the falling edge. Similarly, RX_DV and RX_ER are transmitted on the RX_DV signal line, and RX_DV is transmitted on the rising edge of RX_CLK, and RX_ER is transmitted on the falling edge.
14.3.2 Hardware Design
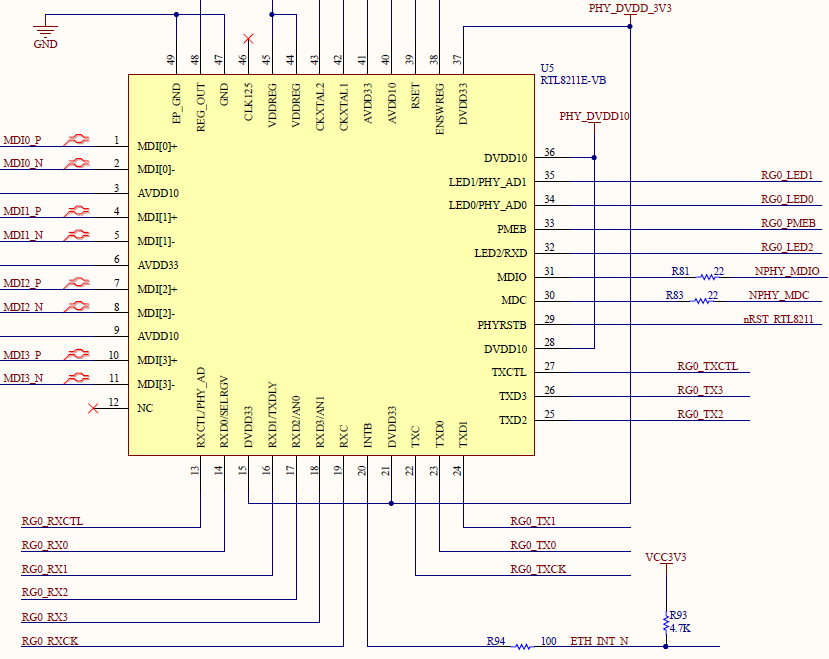
Figure 14.4 Schematics of RTL8211E-VB
The RTL8211E-VB chip is used to form a Gigabit Ethernet module on the experiment board. The schematics is shown in Figure 14.4. The PHY chip is connected to the FPGA by receiving and transmitting two sets of signals. The receiving group signal prefix is RG0_RX, and the transmitting group signal prefix is RG0TX, which is composed of a control signal CTL, a clock signal CK and four data signals 3-0. RG0_LED0 and RG0_LED1 are respectively connected to the network port yellow signal light and green signal light. At the same time, the FPGA can configure the PHY chip through the clock line NPHY_MDC and the data line NPHY_MDIO.
14.3.3 Design of the Program
- Loopback test design (test1)
The first step: introduction to the program
The loopback test is very simple, which just needs to output the input data directly.
|
(Note: Each program in this experiment contains a smi_ctrl module. In the config folder, it is a setting module for the PHY chip, so as to solve the problem that some computers cannot connect to the network port normally, and will not explain in detail)
The second step: pin assignment
Table 14.1 Ethernet Experiment Pin Mapping
| Signal Name | Network Label | FPGA Pin | Port Description |
| rxc | RGMII_RXCK | B12 | Input data clock |
| rxdv | RGMII_RXCTL | A13 | Input data control signal |
| rxd[3] | RGMII_RX3 | A15 | Input data bit 3 |
| rxd[2] | RGMII_RX2 | B14 | Input data bit 2 |
| rxd[1] | RGMII_RX1 | A14 | Input data bit 1 |
| rxd[0] | RGMII_RX0 | B13 | Input data bit 0 |
| txc | RGMII_TXCK | B20 | Output data clock |
| txen | RGMII_TXCTL | A19 | Output data control signal |
| txd[3] | RGMII_TX3 | B18 | Output data bit 3 |
| txd[2] | RGMII_TX2 | A18 | Output data bit 2 |
| txd[1] | RGMII_TX1 | B17 | Output data bit 1 |
| txd[0] | RGMII_TX0 | A17 | Output data bit 0 |
| e_mdc | NPHY_MDC | C17 | Configuration clock |
| e_mdio | NPHY_MDIO | B19 | Configuration data |
Before verification (the default PC NIC is a Gigabit NIC, otherwise it needed to be replaced). PC IP address needs to be confirmed first. In the DOS command window, type ipconfig -all command to check it. Example is shown in Figure 14. 5.
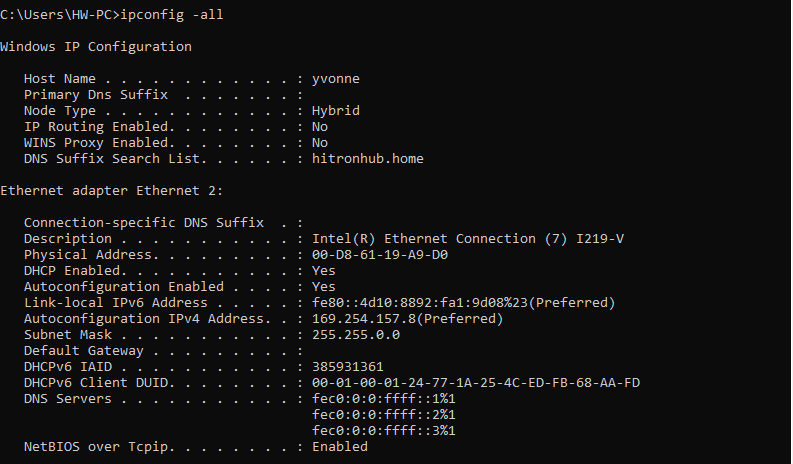
Figure 14.5 PC end IP information
To facilitate subsequent experiments, PC is provided a fixed IP address. Take this experiment as an example, IP configuration is 192.169.0.100(could be revised, but needs to be consistent to the IP address of target sending module, for Internet Protocol reason, IP address 169.XXX.X.X is not suggested). Find Internet Protocol Version 4(TCP/IPv4) in Network and Sharing center. See Figure 14. 6.
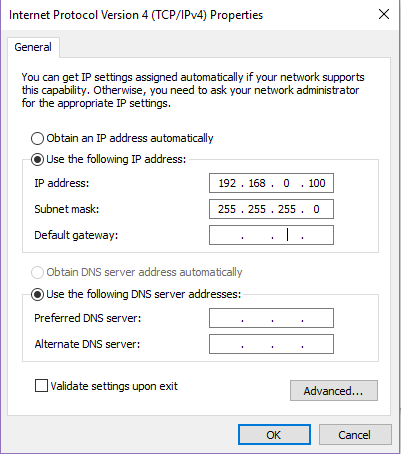
Figure 14.6 Configure PC end IP address
Since there is no ARP protocol content (binding IP address and MAC address of the develop board) in this experiment, it needs to be bound manually through the DOS command window. Here, the IP is set to 192.168.0.2 and the MAC address is set to 00-0A-35-01-FE-C0, (can be replaced by yourself) as shown in Figure 14. 7, the method is as follows: (Note: Run the DOS command window as an administrator)
Run the command: ARP -s 192.168.0.2 00-0A-35-01-FE-C0
View binding results: ARP -a
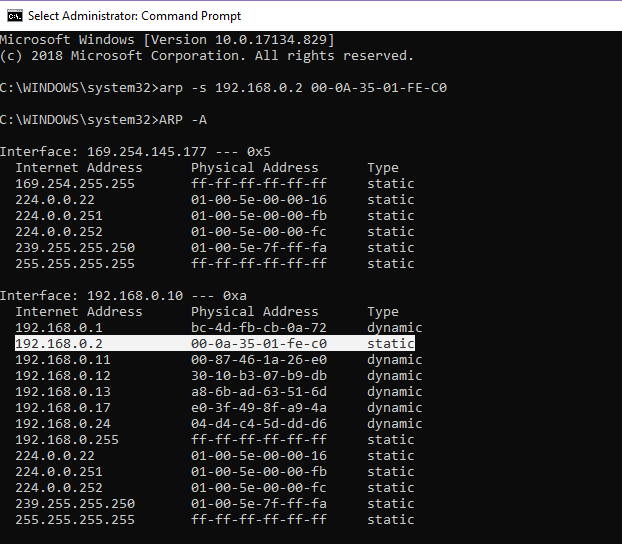
Figure 14.7 Address binding method 1
If a failure occurs while running the ARP command, another way is available, as shown in Figure 14.8:
- Enter the netsh i i show in command to view the number of the local connection, such as the “23” of the computer used this time.
- Enter netsh -c “i i” add neighbors 23 (number) “192.168.0.2” “00-0A-35-01-FE-C0”
- Enter arp -a to view the binding result
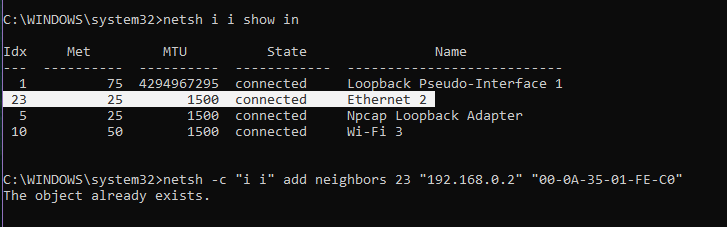
Figure 14.8 Address binding method 2
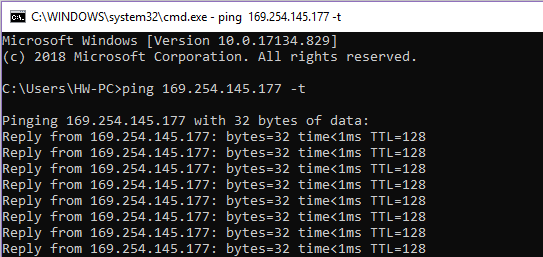
Next, we also use the DOS command window for connectivity detection, as shown in Figure 14. 9. Ping is an executable command that comes with the Windows family. Use it to check if the network can be connected. It can help us analyze and determine network faults. Application format: Ping IP address (not host computer IP).
Start SignalTap II, after sending the command, as shown in Figure 14. 10. The data is ordinary and the hardware is intact seen from the screenshot.
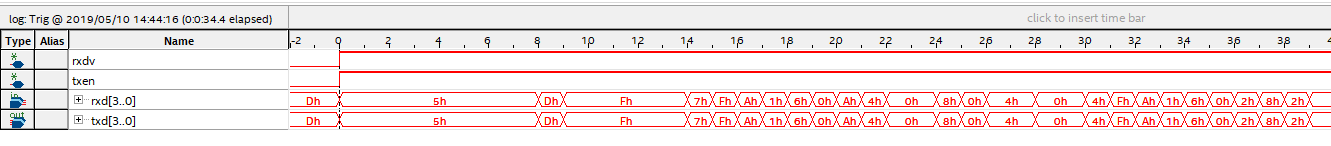
Figure 14.10 SignalTap II data capture
- Special IP core configuration (test2)
Because it is the RGMII interface, the data is bilateral along 4-bit data. Therefore, when data processing is performed inside the FPGA, it needs to be converted into 8-bit data. Go to Installed IP > Library > Basic Functions > I/O to find ALTDDIO_IN and ALTDDIO_OUT. To implement it, IP core (ddio_in) is called, and after internal data processing, IP core is passed (ddio_out) to convert 8-bit data into bilateral edge 4-bit data transfer. It should be noted that, considering the enable signal and data signal synchronization, the enable signal is entered to ddio for conversion at the same time. The specific settings are shown in Figure 14. 11 and Figure 14. 12.
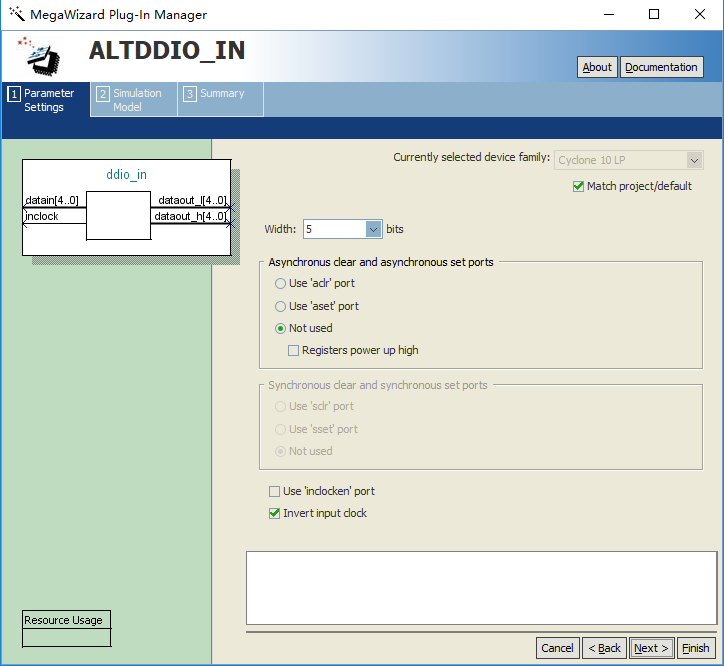
Figure 14.11 ddio_in setting
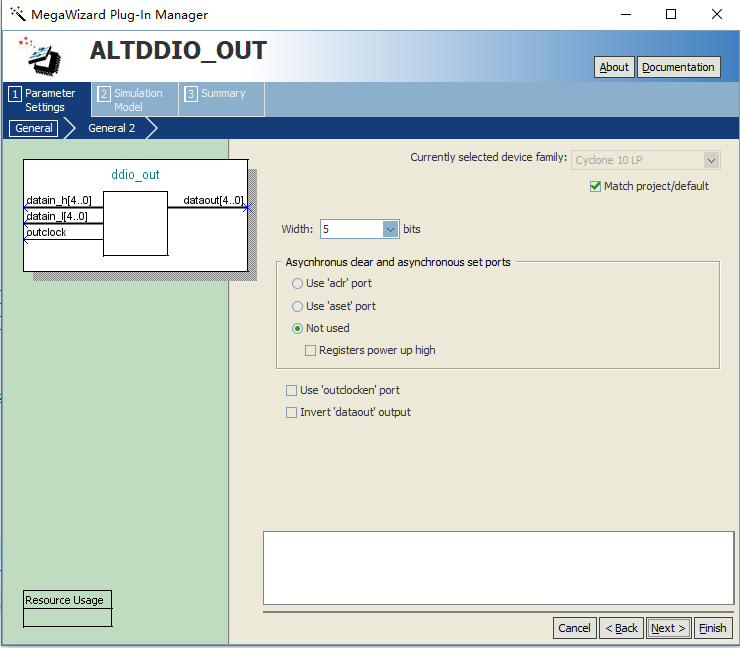
Figure 14.12 ddio_out setting
Considering that the driving ability of the clock provided by the PHY chip is relatively poor, after the phase-locked loop processing, unlike the prior part, the input clock rxc selects the homologous input, as shown in Figure 14. 13, and outputs C0 clock ddio_clk as the driving clock of two ddio IP cores. As shown in Figure 14. 14, outputs the C1 clock txc as the data transmission clock (note that due to hardware circuit and timing reasons, txc needs to be 90° phase difference). See Figure 14. 15.
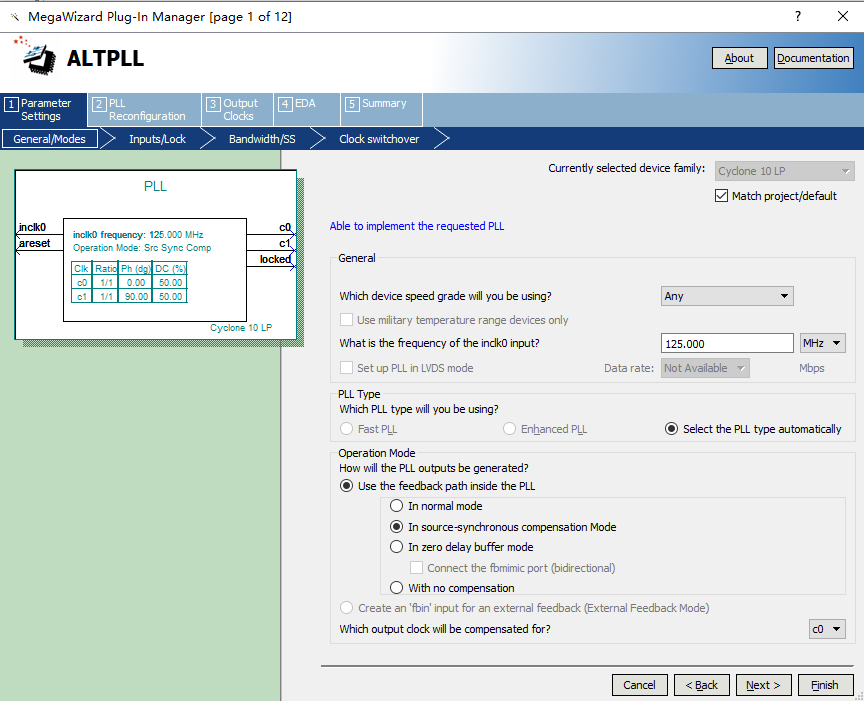
Figure 14.13 PLL input clock setting
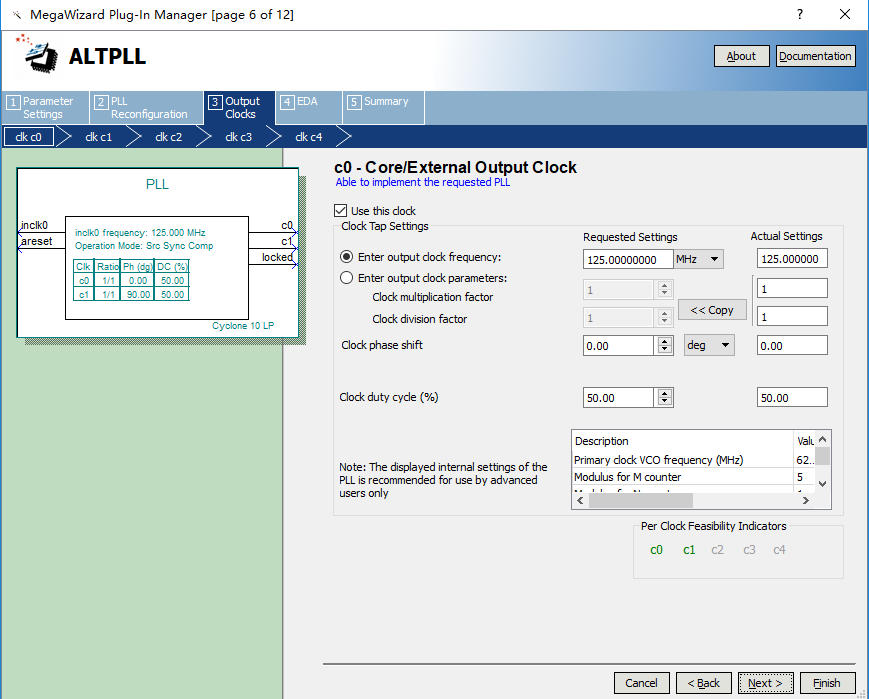
Figure 14.14 PLL output clcok(c0) setting
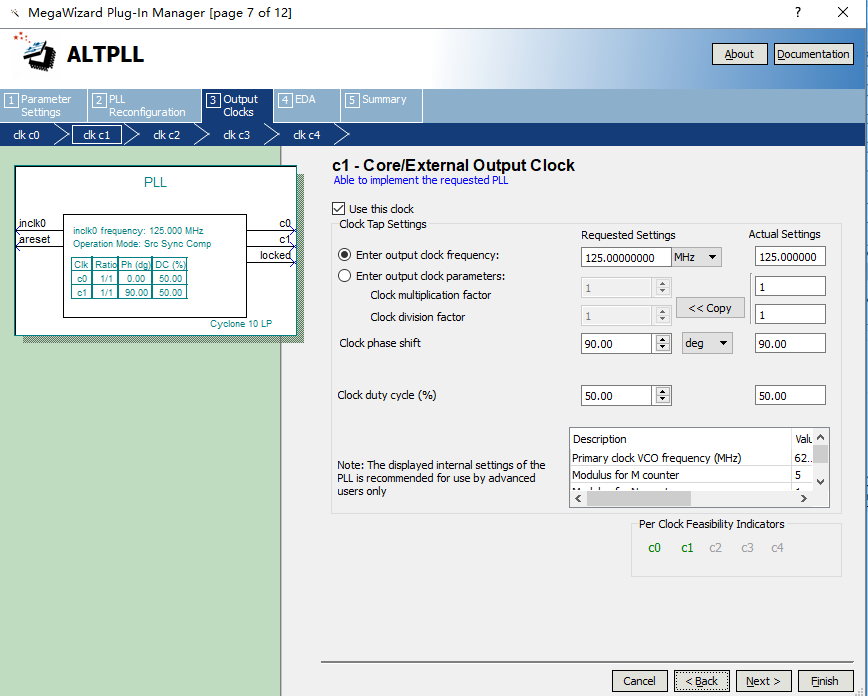
Figure 14.15 PLL output clcok(c1) setting
The three IP cores are instantiated into the previous loopback test, and the data transmission correctness test is performed. (It is necessary to notice the ordered timing. The ddio_out input data needs to be reversed. For details, refer to the project file (test2)). This time a network debugging assistant applet is used as an auxiliary testing tool. Program the board and verify it.
As shown in Figure 14.16, after setting the correct address and data type, we send the detection information (love you!) through the host computer. The data packet is captured by Wireshark, as shown in Figure 14.17. The data is correctly transmitted back to the PC.
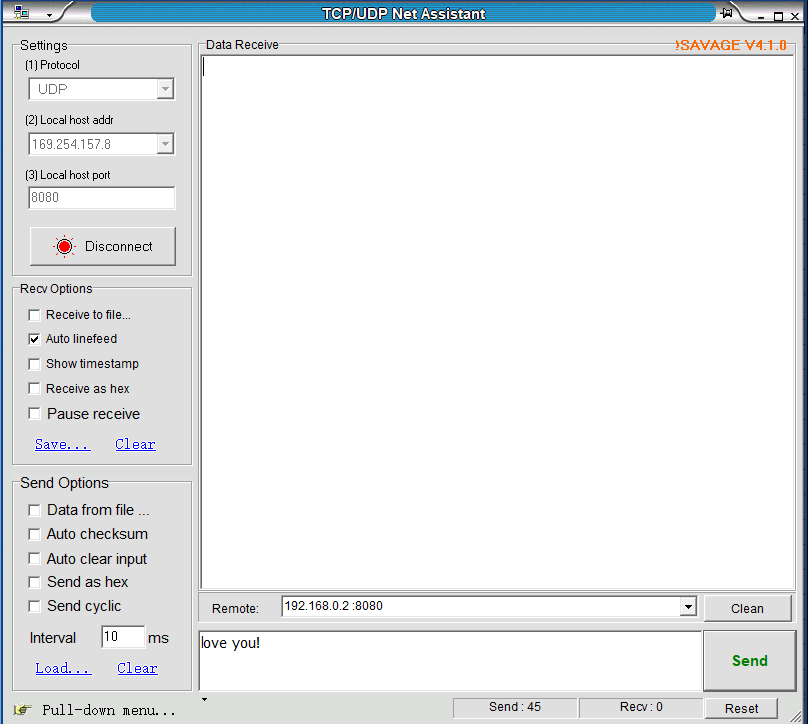
Figure 14.16 Host computer sends the test data
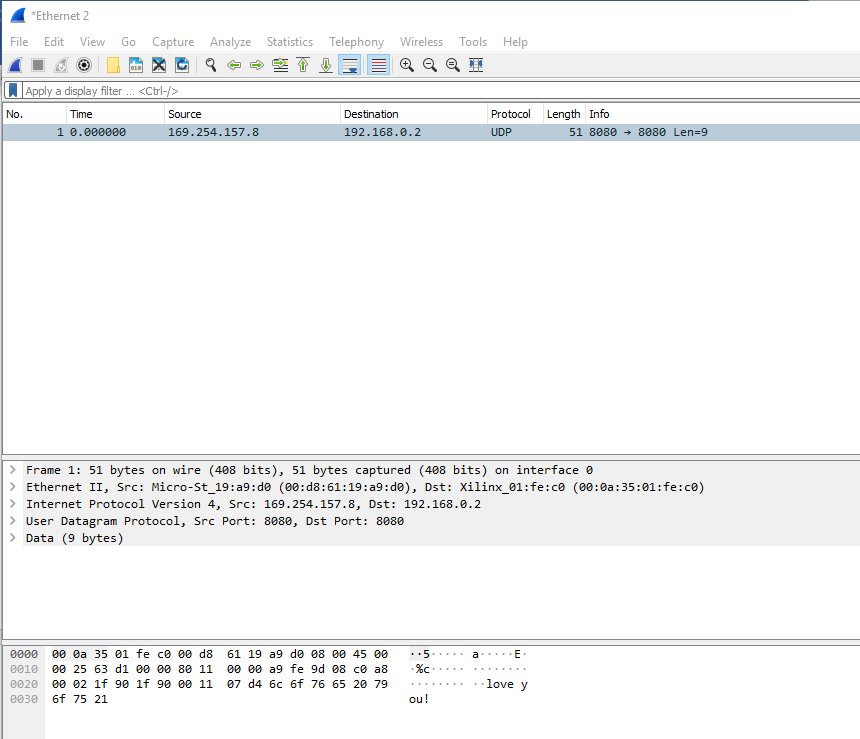
Figure 14.17 Correct reception of data on the PC side
- Complete Ethernet data transmission design
For complete Ethernet data transmission, it is necessary to have the receiving part of the data and the transmitting part of the data. For the convenience of experiment, we store the data transmitted by the PC first in the RAM. After reading via the transmitting end, send it to the PC. For a series of data unpacking and packaging, refer to the project file “ethernet”. A brief introduction to each module follows.
- Data receiving module (ip_receive)
The problem to be solved by this module is to detect and identify the data frame, unpack the valid data frame, and store the real data in the ram.
|
The receiving module is to perform step by step analysis on the received data.
Idle state: If ‘55’ is received, it jumps to the six_55 state.
Six_55 state: If it continues to receive six consecutive 55s, it will jump to the spd_d5 state, otherwise it will return the idle state.
Spd_d5 state: If ‘d5’ continues received, it proves that the complete packet preamble “55_55_55_55_55_55_55_d5” has been received, and jumps to rx_mac, otherwise it returns the idle transition.
rx_mac state: This part is the judgment of the target MAC address and the source MAC address. If it matches, it will jump to the rx_IP_Protocol state, otherwise it will return the idle state and resend.
rx_IP_Protocol state: Determine the type and length of the packet and jump to the rx_IP_layer state.
rx_IP_layer state: Receive 20 bytes of UDP virtual header and IP address, jump to rx_UDP_layer state
rx_UDP_layer state: Receive 8-byte UDP port number and UDP packet length, jump to rx_data state
Rx_data state: Receive UDP data, jump to rx_finish state
Rx_finish state: A packet of data is received, and it jumps to the idle state to wait for the arrival of the next packet of data.
- Data sending module (ip_send)
The main content of this module is to read out the data in the RAM, package and transmit the data with the correct packet protocol type (UDP). Before transmitting, the data is also checked by CRC.
|
This part defines the preamble of the data packet, the MAC address of the PC, the MAC address of the development board, and the IP packet type. It should be noted that in the actual experiment, the MAC address of the PC needs to be modified. Keep the MAC address consistent along the project, otherwise the subsequent experiments will not receive data.
|
Idle state: Waiting for delay, sending a packet at regular intervals and jumping to the start state.
Start state: Send the packet header and jump to the make state.
make state: Generates the checksum of the header and jumps to the send55 state.
Send55 status: Send 8 preambles and jump to the sendmac state.
sendmac state: Send the target MAC address, source MAC address and IP packet type, and jump to the sendheader state.
sendheader state: Sends 7 32-bit IP headers and jumps to the senddata state.
senddata state: Send UDP packets and jump to the sendcrc state.
sendcrc state: Sends a 32-bit CRC check and returns the idle state.
Following the above procedure, the entire packet of data is transmitted, and the idle state is returned to wait for the transmission of the next packet of data.
- CRC check module (crc)
The CRC32 check of an IP packet is calculated at the destination MAC Address and until the last data of a packet. The CRC32 verilog algorithm and polynomial of Ethernet can be generated directly at the following website: http://www.easics.com/webtools/crctool
- UDP data test module (UDP)
This module only needs to instantiate the first three sub-modules together. Check the correctness of each connection.
- Top level module settings (ethernet)
The PLL, ddio_in, ddio_out, ram, and UDP modules are instantiated to the top level entity, and specific information is stored in advance in the RAM (Welcome To ZGZNXP World!). When there is no data input, the FPGA always sends this information. With data input, the received data is sent. Refer to the project files for more information.
14.4 Experiment Verification
The pin assignment of this test procedure is identical to that in Test 1.
Before programming the development board, it is necessary to note that the IP address of the PC and the MAC address of the development board must be determined and matched, otherwise the data will not be received.
Download the compiled project to the development board. As shown in Figure 14.18, the FPGA is keeping sending information to the PC. The entire transmitted packet can also be seen in Wireshark, as shown in Figure 14.19.
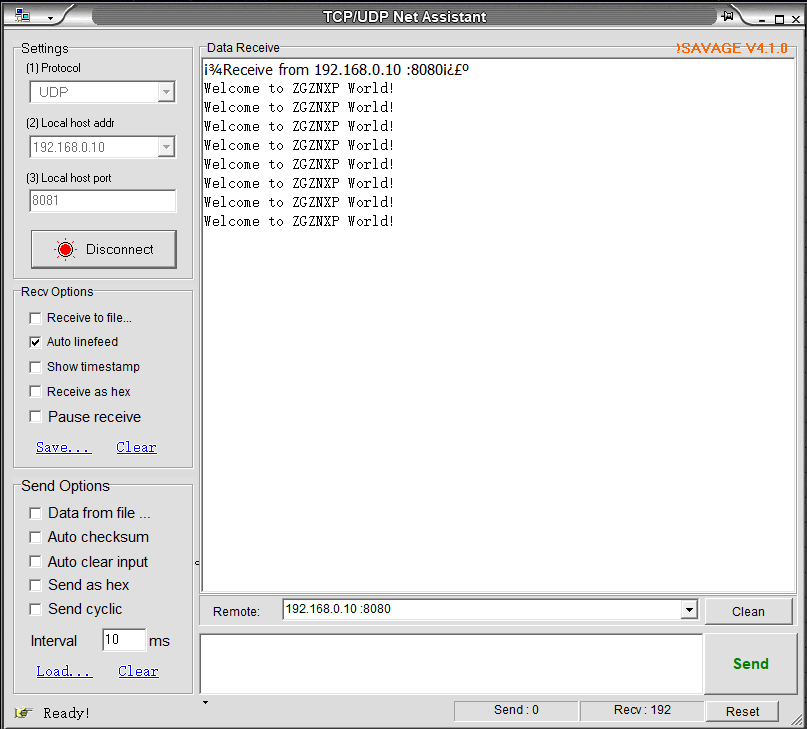
Figure 14.18 Send specific information
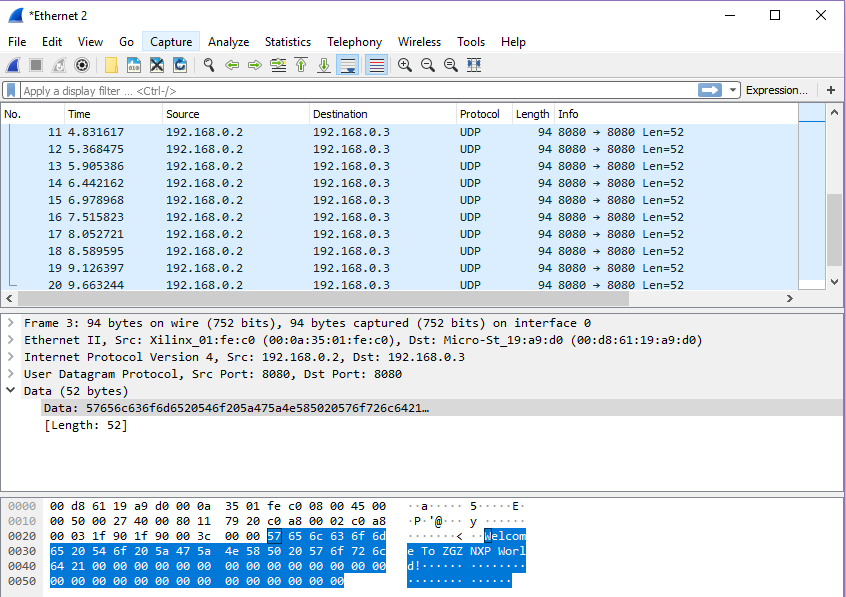
Figure 14.19 Specific information package
When the PC sends data to the FPGA, as shown in Figure 14. 20, the entire packet arrives at the FPGA, and then the FPGA repackages the received data and sends it to the PC. See Figure 14. 21, the network assistant also receives the transmitted data information accurately, as shown in Figure 14. 22. Similarly, through SignalTap we can see the process of writing the received data, as shown in Figure 14. 23.
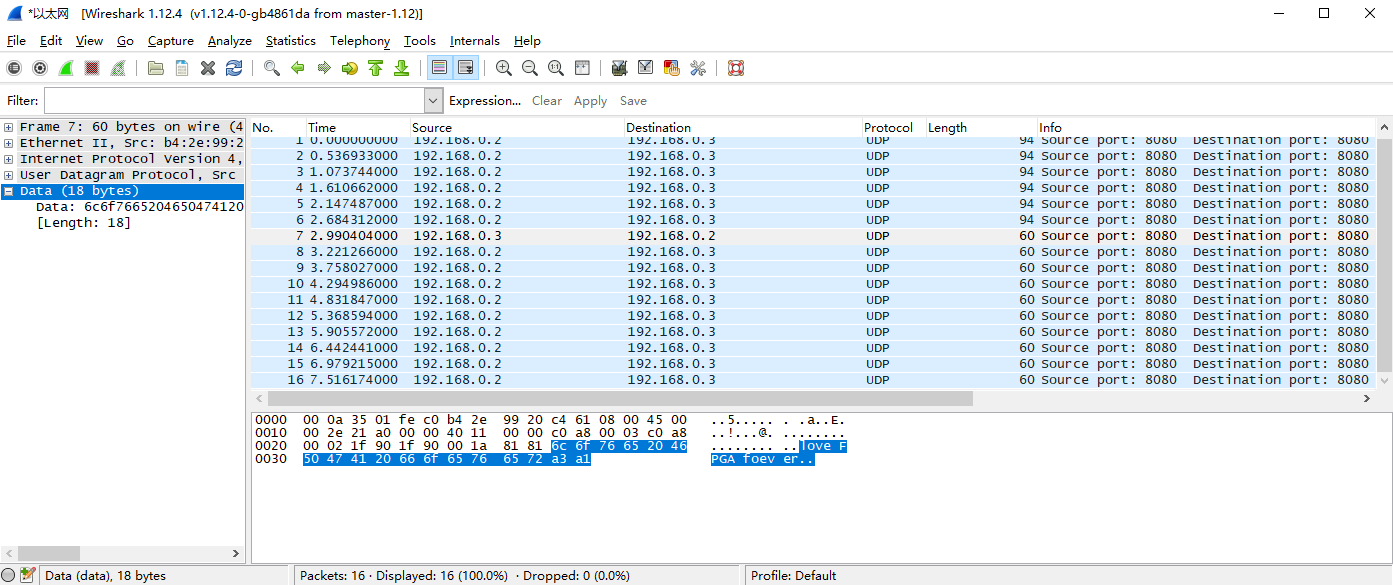
Figure 14. 20 PC send data package
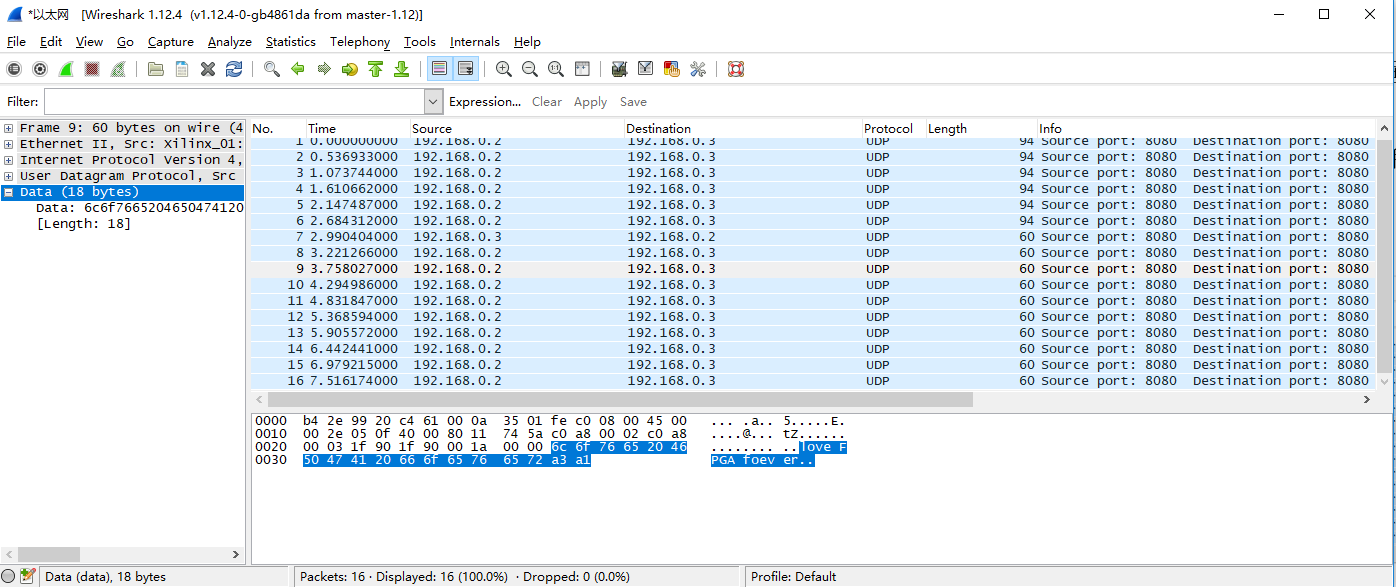
Figure 14.21 The FPGA repackages the received data and sends it to the PC
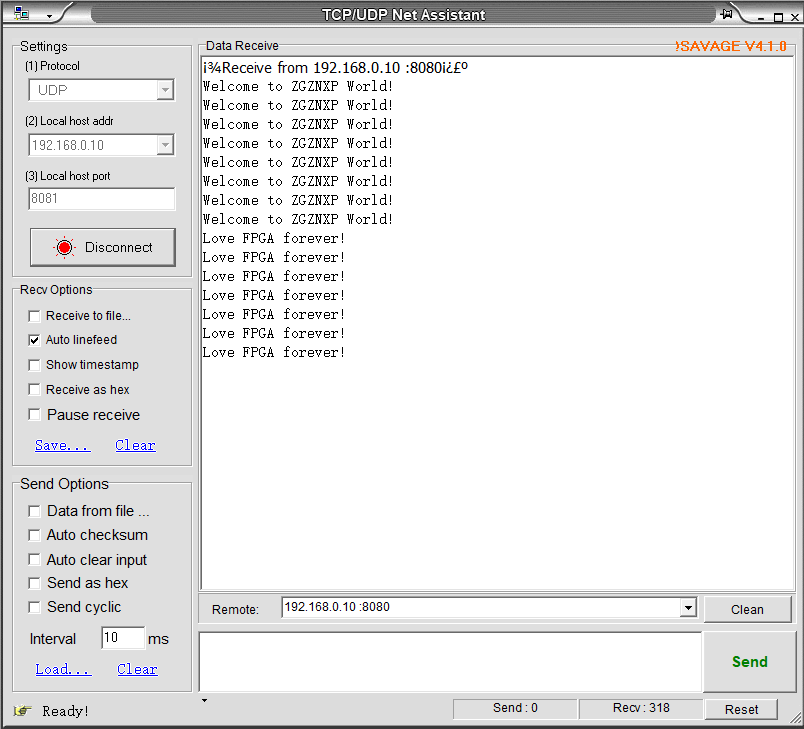
Figure 14.22 Information received by PC from FPGA
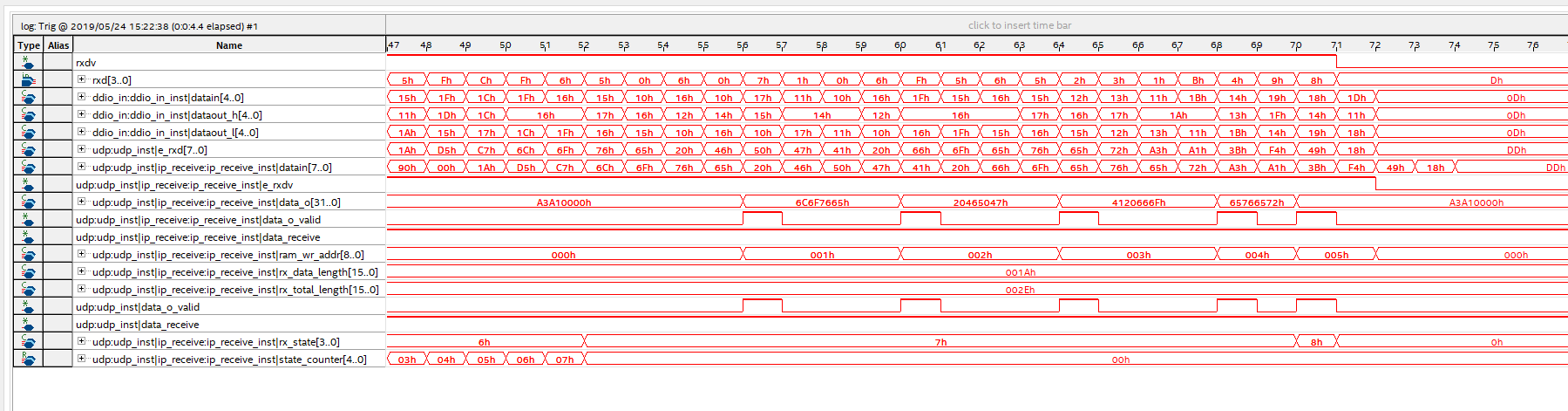
Figure 14.23 FPGA end data and stored in the RAM process
It should be noted that Ethernet II specifies the Ethernet frame data field is a minimum of 46 bytes, that is, the minimum Ethernet frame is 6+6+2+46+4=64. The 4-byte FCS is removed, so the packet capture is 60 bytes. When the length of the data field is less than 46 bytes, the MAC sublayer is padded after the data field to satisfy the data frame length of not less than 64 bytes. When communicating over a UDP LAN, “Hello World” often occurs for testing, but “Hello World” does not meet the minimum valid data (64-46) requirements. It is less than 18 bytes but the other party is still available for receiving, because data is complemented in the MAC sublayer of the link layer, less than 18 bytes are padded with ‘0’s. However, when the server is on the public network and the client is on the internal network, if less than 18 bytes of data is transmitted, the receiving end cannot receive the data. Therefore, if there is no data received, the information to be sent should be increased to more than 18 bytes.